Qu’est ce que Jenkins ?
Jenkins est un outil open source d’intégration continue, fork de l’outil Hudson après les différends entre son auteur, Kohsuke Kawaguchi, et Oracle. Écrit en Java, Jenkins fonctionne dans un conteneur de servlets tel qu’Apache Tomcat, ou en mode autonome avec son propre serveur Web embarqué.
Il s’interface avec des systèmes de gestion de versions tels que CVS, Git et Subversion, et exécute des projets basés sur Apache Ant et Apache Maven aussi bien que des scripts arbitraires en shell Unix ou batch Windows.
Les générations de projets peuvent être amorcées par différents moyens, tels que des mécanismes de planification similaires au cron, des systèmes de dépendances entre générations, ou par des requêtes sur certaines URL spécifiques.
Autour de 2008, Jenkins est devenu une solution de remplacement populaire3 à l’outil de référence CruiseControl.
Source
Comment ca fonctionne ?
Tout commence avec un serveur Maître, sur lequel viennent se connecter les Agents :
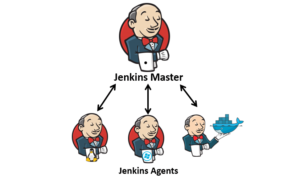
Le Serveur Maître va lancer differnets Tâches sur ces agents (construction d’applications, preparation d’environnements, déploiements …)
pour plus d’informations voir le site officiel jenkins.io
Installation
Prérequis
- Avoir Docker installer et fonctionnel sur son serveur
Serveur Maître
lancer le docker jenkins avec la commande suivante :
docker run -d -name JenkinsMaster -p 8080:8080 -p 50000:50000 -v jenkins_home:/var/jenkins_home jenkins/jenkins:ltsOu Jenkins_home doit être remplacer par le chemin de votre choix (cela permettra d’avoir acces a la configuration ulterieurement)
Plus d’informations sur ce docker et ces paramètres sur le Github de Jenkins.
Serveur Agent (nodes)
Agents SSH
Configuration coté Maître
Génération des clefs SSH
Pour deployer des agents SSH il faut créer des cléfs de chiffrements public et privé sur le serveur Maître.
Pour cela connecter vous à une console sur le docker JenkinsMaster :
docker exec -it JenkinsMaster /bin/bashCe connecter en tant que jenkins:
su - jenkins
ssh-keygen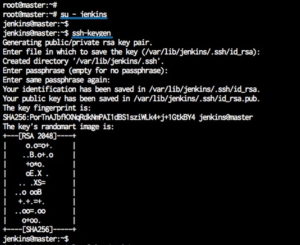
Saisir une PassPhrase et bien l’enregistrer pour plus tard.
Ajout de l’utilisateur dans Jenkins
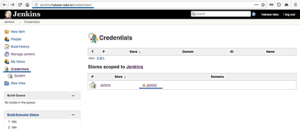
Dans Jenkins, aller dans Crédentials, et cliquer sur global:
Puis cliquer sur Add Credentials, et saisir les infos du compte :
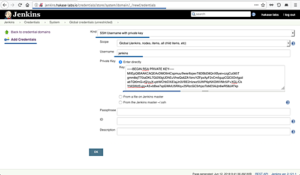
Type de compte : selectionner SSH Usernanme with private key
Scope : Global
Username: jenkins
Private Key : saisir la clef privé (id_rsa) obtenu à l’étape précédente.
Dans le docker JenkinsMaster vous la trouverez en tapant la commande suivante :
cat /var/jenkins_home/.ssh/id_rsaPassPhrase : Saisir la PassPhrase saisie au moment de la génération de la clef
Puis cliquer enfin sur OK, votre utilisateur est configuré sur votre Maître.
Installation de « l’Agent » SSH
Comme pour la Master cette agent fonctionnera sous Docker.
Pour le lancer il suffit d’éxécuter la commande suivante :
docker run jenkins/ssh-slave "<public key>"Remplacer <public key> par la clef publique obtenue sur le Maître
Sur le serveur Maître executer la commande suivante pour afficher la clef :
cat /var/jenkins_home/.ssh/id_rsa.pubPlus d’informations sur ce docker et ces paramètres sur le Github de Jenkins.
Configuration du nouveau noeud dans Jenkins
Se rendre dans Manage, puis Manage Nodes, faire Add Nodes :
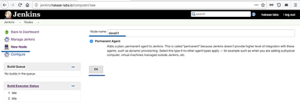
Choisir permanent agent, et lui donner un nom (ssh-slave01 par exemple), cliquer ensuite sur OK
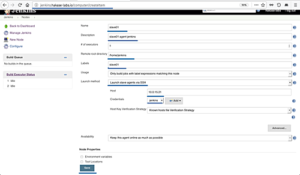
Saisir les informatiosn suivantes:
- Remote root directory: /home/jenkins
- Labels: slave01
- Launch method: Launch slave agent via SSH
- Entrer l’addresse IP de votre agent (ici celui de notre hôte Docker)
- Selectionner le crédential ‘Jenkins’ créer précédement.
- Host Key Verification Strategy Selectionner Manually Trusted key verification Startegy (il vous seras demander de la valider au premier lancement du Noeud)
Aller dans Advanced, si vous avez modifier le port ssh du docker agent, remplacer 22 par lecelui que vous avez choisi.
Saisir le JavaPath avec : /usr/local/openjdk-8/bin/java
Cliquer enfin sur Enregistrer.
Démarrage du Noeud
Dans la liste des noeud disponible, selectionner le noeud nouvellement créer et cliquer sur Launch.
Dans le menu gauche, une nouvelle ligne apparait vous demandant de valider la clef de connexion, cliquer dessus et accepter.
Votre Agent est maintenant démarrer.
Source :
https://www.howtoforge.com/tutorial/ubuntu-jenkins-master-slave/
https://jenkins.io/
https://www.docker.com/



